Evilginx 102: Hacker’s Blueprint - Building the Ultimate Phishing Infra

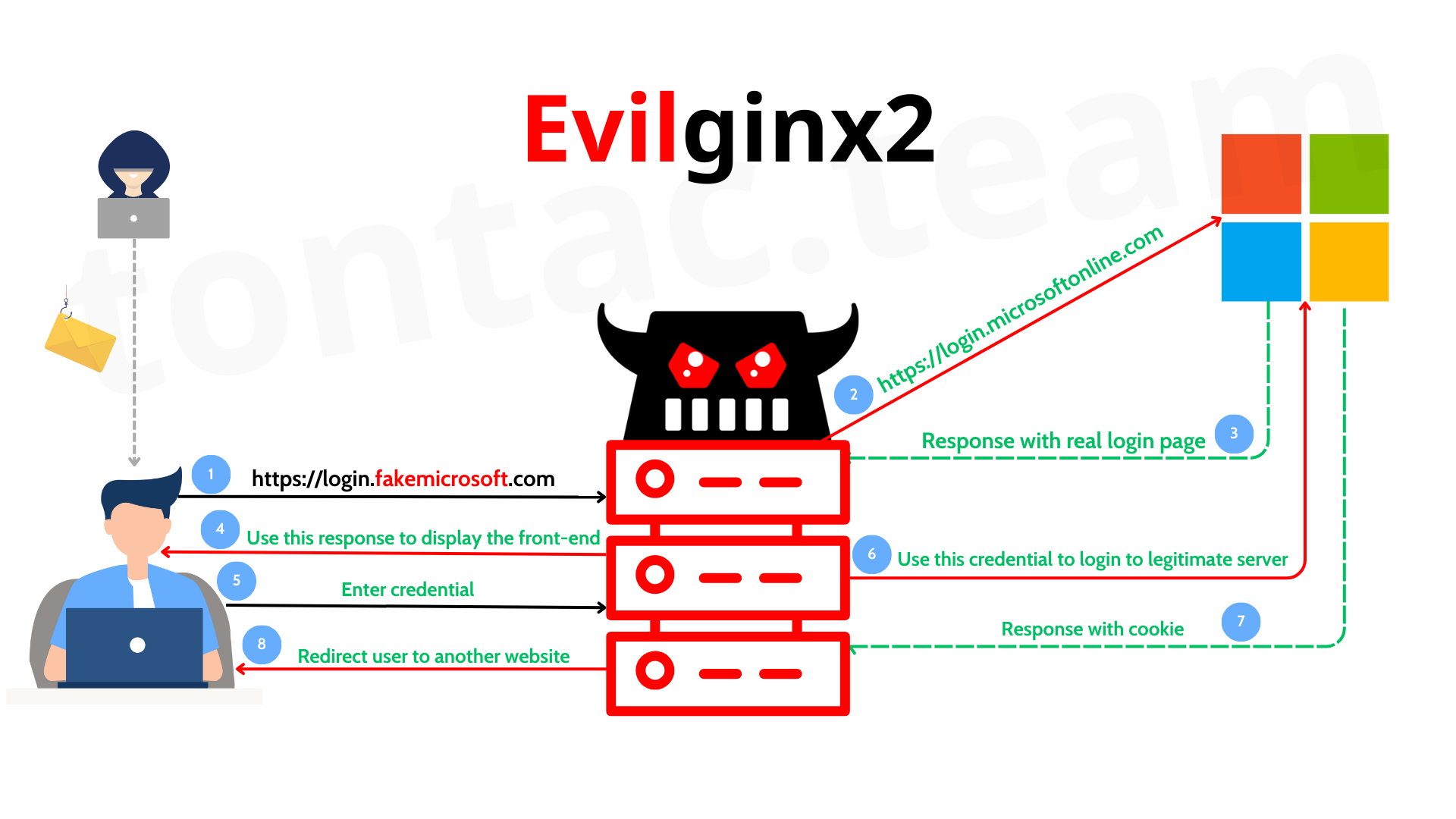
In our previous post, Evilginx 101: Introduction to Modern Phishing & Adversary-in-the-Middle Attacks, we explored how Evilginx works as a powerful Adversary-in-the-middle (AitM) framework for phishing attacks. Now, let’s dive deeper into the attacker’s perspective and understand how to build an effective phishing infrastructure that can bypass multi-factor authentication (MFA) and remain undetected for as long as possible.
1. Setting Up the Infrastructure
To create a robust phishing operation, an attacker needs a secure and scalable infrastructure. Here are the key components:
1.1. VPS and Domain Setup
An attacker typically starts by acquiring a Virtual Private Server (VPS) and a domain that closely resembles the target organization.
- Choosing a VPS provider: Services like DigitalOcean, Linode, or AWS are commonly used due to their reliability and flexibility.
- Registering a deceptive domain: Attackers often use homoglyphs (e.g.,
g00gle.cominstead ofgoogle.com) or subdomains (login.example.com). - Configuring DNS records: We will let our domain go through CloudFlare to hide our IP Address.
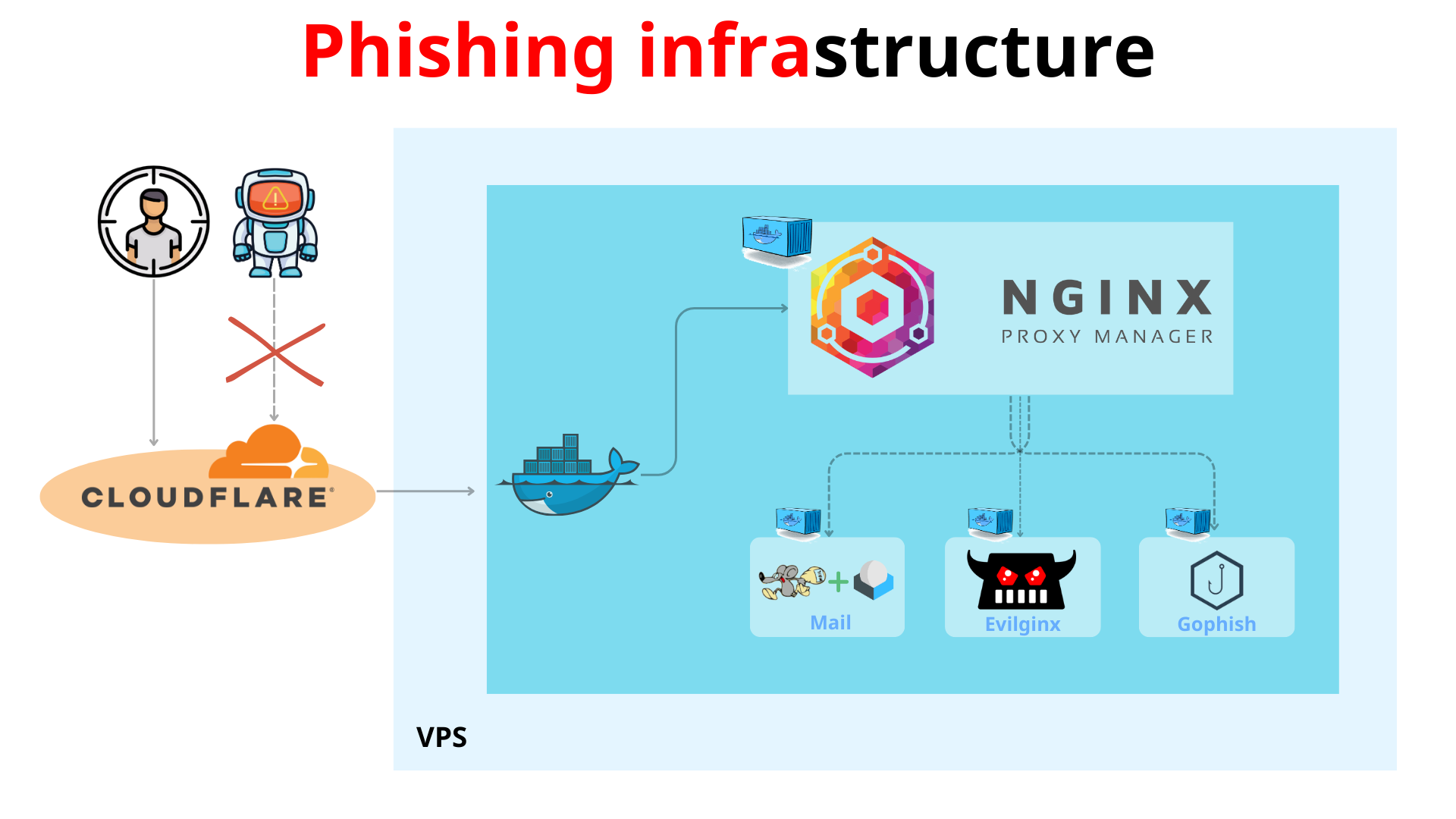
1.2. Phishing Infrastructure Overview
A well-structured phishing infrastructure typically consists of multiple layers to avoid detection and increase efficiency. The setup includes:
- Cloudflare Protection: Used to hide the real VPS IP and filter unwanted traffic.
- Dockerized Services: Running Evilginx, Roundcube (a webmail service), and phishing-related tools in isolated containers.
- Nginx Proxy Manager: Managing and routing traffic between different components securely.
This infrastructure ensures that only legitimate traffic is allowed while attackers can control stolen data efficiently.
2. The Role of Cloudflare in Phishing Infrastructure

Cloudflare is a crucial component in this setup, providing multiple advantages for attackers
2.1 IP Masking:
Cloudflare acts as an intermediary, hiding the real VPS IP address and preventing security teams from tracing the phishing site directly. By routing all traffic through Cloudflare, attackers prevent their VPS IP from being exposed.
When security teams detect a phishing page, they attempt to trace its real hosting provider to request a takedown or report the phishing page IP to a database.
So when you're got flagged as phishing, the domain and the real IP will also be flagged, CloudFlare help us to not change our vps each time we got flaged.
2.2 DDoS Protection:
Once a phishing site is detected, the security team of the targeted organization may attempt to take it down through a DDoS attack. We don't want manually create our WAF to prevent this kind of attack, so Cloudflare provides DDoS protection that makes it difficult for defenders to shut down the phishing page
2.3 WAF (Web Application Firewall) Bypass:
Attackers often configure Cloudflare rules to bypass WAF restrictions that could otherwise flag their phishing domains.
Attackers configure Cloudflare’s firewall rules to neutralize WAF detection and keep phishing pages accessible to their victims:
- Custom Firewall Rules to Block Security Scanners
Attackers use Cloudflare’s WAF custom rules to block incoming requests from known security firms, threat intelligence providers, and automated scanners like: Google Safe Browsing (GSB), VirusTotal URL Scanners, PhishTank, etc.
We know that the GSB is very powerful method to prevent user from a phishing attack.
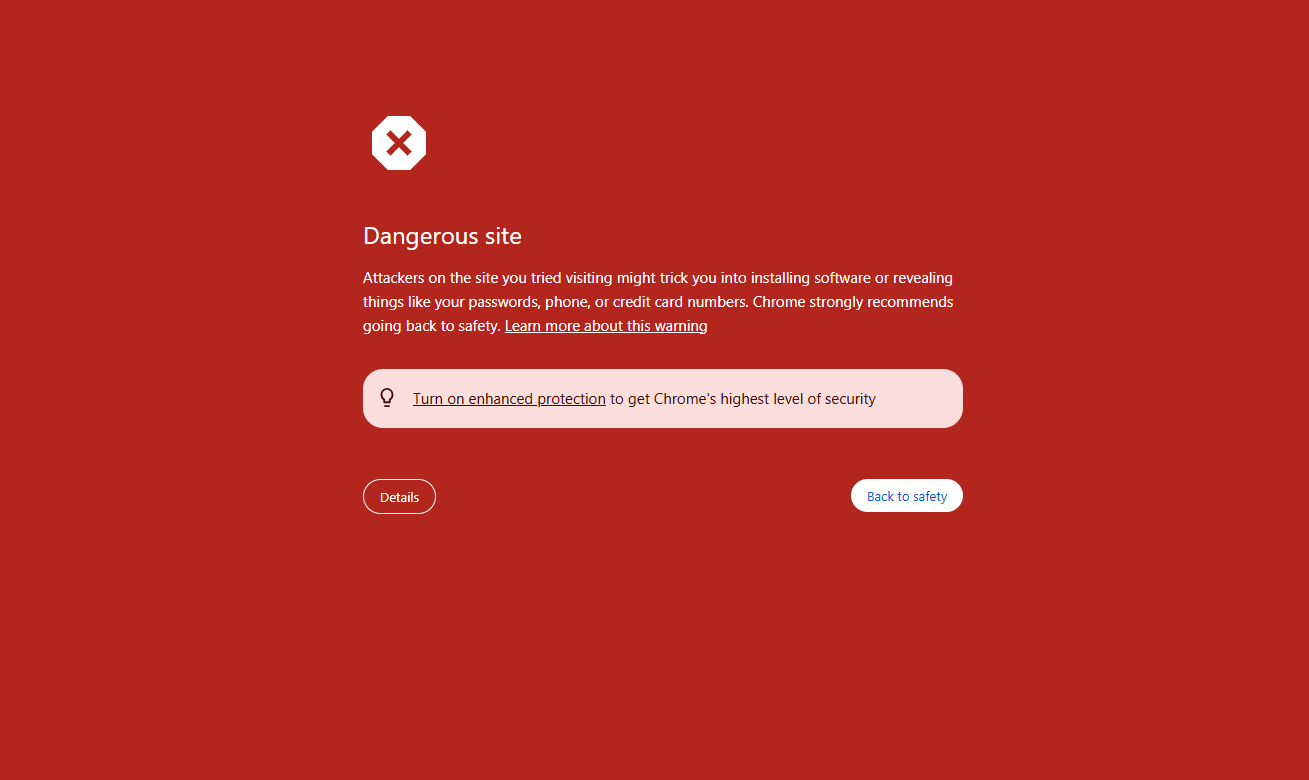
Surely even a user with little knowledge of security will be cautious when accessing these websites marked as phishing. (A blog about how GSB works will be released soon).
- Geofencing to Limit Access
Attackers restrict access to the phishing page by allowing only victims from specific geographic locations. Security teams (often analyzing phishing sites from the U.S. or Europe) get blocked automatically, preventing them from collecting evidence.
Eg: When you're performing a campaign for a company in Vietnam, you don't want other countries access the phishing page.
- User-Agent & Referrer Filtering
Security tools often use non-standard User-Agent strings (e.g., curl, wget, Mozilla/5.0 (compatible; Googlebot/2.1)). Attackers set Cloudflare rules to block requests from security tool user-agents while allowing normal browser traffic.
- CAPTCHA Challenges for Unknown Visitors
Attackers configure Cloudflare’s JavaScript challenges or CAPTCHA prompts to disrupt automated analysis by WAFs. Legitimate victims seamlessly access the phishing page, while automated bots fail the challenge and get blocked.
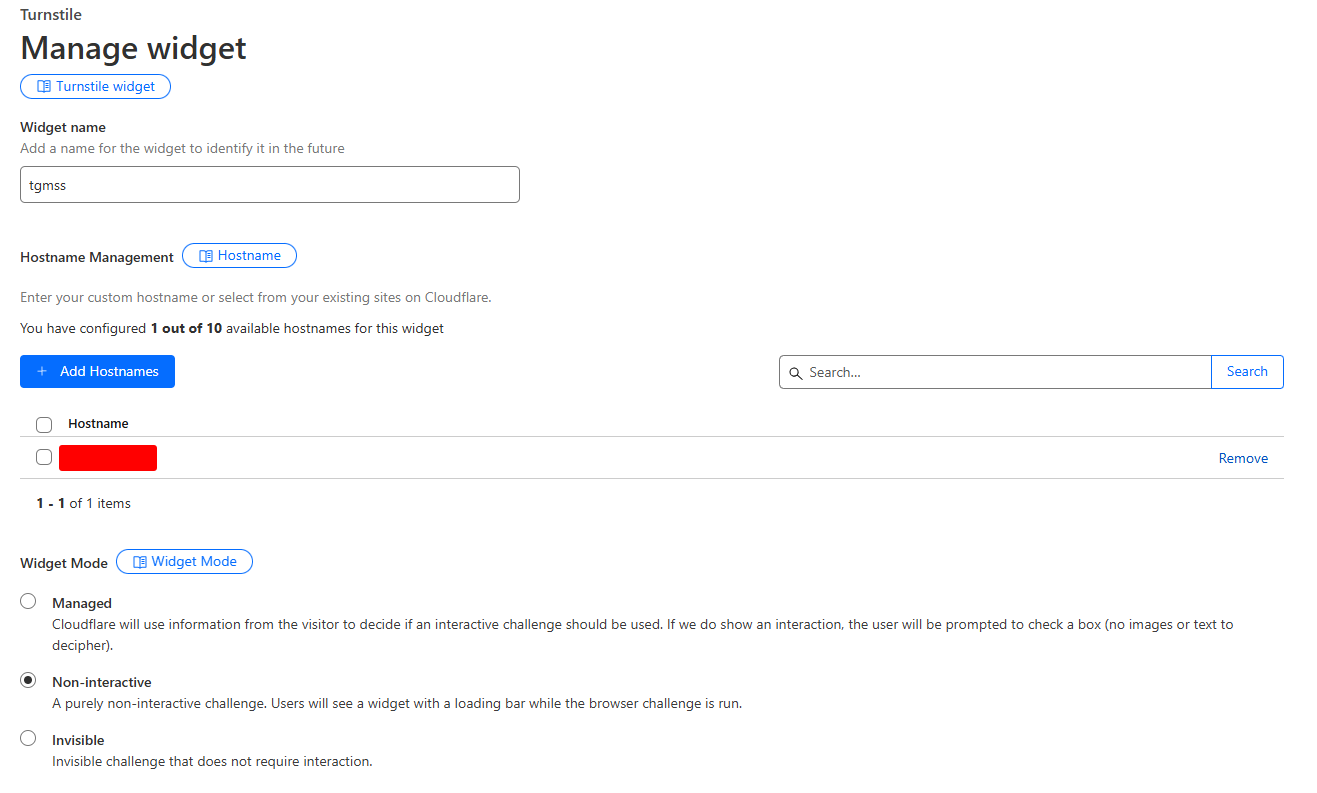
Turnstile is a feature of CloudFlare, it uses various techniques, including behavioral analysis and device fingerprinting, to determine if a user is human.
You can see that there are 3 mode, you can choose the mode that best fit with your campaign.
3. Mailing service

To send emails, GoPhish requires valid SMTP credentials for an SMTP server. While it may be tempting to set up your own SMTP server, this is generally discouraged because established email service providers (such as Gmail, Outlook, or SendGrid) invest heavily in maintaining high sender reputations. These services ensure emails are delivered directly to inboxes rather than being flagged as spam.
Why Avoid Setting Up an SMTP Server from Scratch?
When you configure a new SMTP server, it lacks a sending reputation. Email providers use various filters to determine whether an email is legitimate, and messages sent from a fresh SMTP server often get marked as spam or even blocked entirely. This happens because spammers frequently use new servers to send phishing or malicious emails, prompting email providers to be extra cautious with unverified domains.
Additionally, managing an SMTP server requires constant monitoring and configuration, including:
- Reverse DNS (PTR records): Some mail servers reject emails from IPs without a valid reverse DNS record.
- SPF (Sender Policy Framework): Helps verify that your server is authorized to send emails on behalf of your domain.
- DKIM (DomainKeys Identified Mail): Adds a cryptographic signature to your emails to prove their authenticity.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): Defines how email providers should handle emails that fail SPF or DKIM checks.
- IP Reputation Management: ISPs track IP reputation, and a bad reputation can lead to emails being blocked.
- SMTP Rate Limits & Throttling: Many ISPs limit the number of emails a new server can send per hour/day.
If you want your phishing emails to have the highest chance of landing in the victim's inbox instead of the spam folder, it's best to use the same email provider as your target.
For example, if your victim uses Outlook (Microsoft 365), you should purchase a Microsoft 365 account and configure GoPhish to send emails through it. This significantly reduces the likelihood of your emails being flagged as spam
To configure GoPhish to send emails through a Google account, you must:
- Enable 2FA (Two-Factor Authentication) on your Google account.
- Generate an App Password in Google’s security settings. <https://myaccount.google.com/apppasswords>
- Use the App Password instead of your regular password when setting up the SMTP server in GoPhish.
This same process applies if you're using Outlook (Microsoft 365) <https://support.microsoft.com/en-us/account-billing/how-to-get-and-use-app-passwords-5896ed9b-4263-e681-128a-a6f2979a7944>
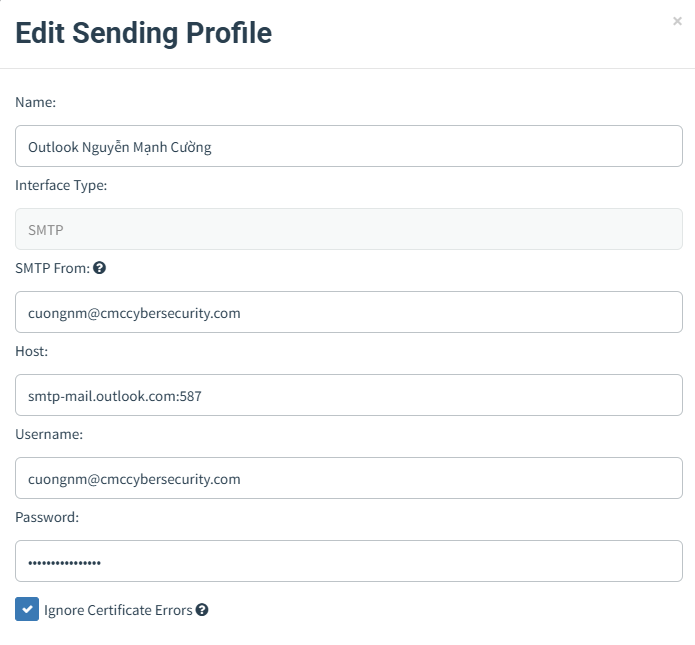
When Does Running Your Own SMTP Server Make Sense?
If you prefer a cost-effective, self-hosted solution, you can use Postfix as the SMTP server and Roundcube as the web-based email client. Both are open-source tools that allow you to manage your own email infrastructure while reducing expenses. Though this approach requires additional configuration to maintain deliverability, such as proper DNS records (SPF, DKIM, and DMARC), it can be a viable alternative to commercial SMTP services.
4. Dockerizing the Phishing Infrastructure

To improve scalability, maintainability, and stealth, attackers often containerize their phishing infrastructure using Docker. This enables the deployment of Evilginx, Nginx Proxy Manager, and auxiliary services in isolated, easily replicable, and more secure environments.
Since vulnerabilities (CVEs) in Evilginx, Gophish, or other components can emerge unexpectedly, running them in Docker minimizes the risk of a full system compromise.
Each container operates within an isolated network, allowing internal communication while remaining hidden from direct internet exposure. All external requests are first routed through Nginx Proxy Manager, ensuring controlled access and additional filtering.
So, in this infrastructure:
- Roundcube serves as the webmail interface.
- Postfix as a mail server.
- Evilginx acts as a reverse proxy to intercept and relay credentials.
- GoPhish is responsible for crafting and sending phishing emails.
However, the journey of phishing doesn't end here. Attackers must overcome several challenges, including Google Safe Browsing detection, email deliverability issues (junk/spam filters), Sender Confidence Level (SCL), crafting convincing email content.
These obstacles require advanced techniques and constant adaptation. I'll cover them in detail in upcoming posts.
Stay tuned ! 🚀
Or if you want to build a phishing-as-a-service platform, you can check it out here:

References:

https://www.cloudflare.com/learning/email-security/dmarc-dkim-spf/





