Evilginx 103: Google’s Defenses - A Deep Dive into Safe Browsing

In the Evilginx series, we’ve explored the power of adversary-in-the-middle (AiTM) phishing and how attackers can leverage Evilginx2 to bypass traditional authentication mechanisms. In Evilginx 101, we broke down the fundamentals of modern phishing, explaining how AiTM techniques allow attackers to intercept and steal session cookies. Then, in Evilginx 102, we went deeper, setting up an advanced phishing infrastructure optimized for stealth and efficiency.
However, as phishing techniques evolve, so do the defenses built to counter them. One of the biggest challenges for attackers today is Google Safe Browsing (GSB), Google’s security system designed to identify and block phishing sites in real time. Integrated into Chrome, Firefox, Safari, and even mobile security solutions, GSB acts as a crucial barrier that prevents users from accessing malicious domains.
So the question arises: How does Google Safe Browsing detect phishing websites? And how do attackers manage to bypass it?
This post will demystify Google Safe Browsing’s detection methods and reveal attackers' stealth tactics to evade it.

Google Safe Browsing Dig Deep
1.1 What is Google Safe Browsing?
Beyond just blocking phishing sites, Safe Browsing also protects against:
- Malware distribution (sites that spread trojans, keyloggers, and ransomware)
- Unwanted software (PUPs, ad injectors, and spyware)
GSB continuously updates its database of malicious URLs, flagging new threats as they emerge. However, the real power of Safe Browsing lies in Google’s advanced AI-driven threat detection, which allows it to identify phishing attempts even before they gain widespread recognition.
2.2 How Google Identifies Phishing Sites
Safe Browsing crawls and analyzes the web to discover potentially harmful sites and adds them to its lists. Each time you visit a website or attempt a download, Chrome checks with Safe Browsing based on the protection level you've selected.
There are three modes of protection:
- Enhanced protection: Google’s most secure browsing experience. Enhanced protection offers security from known and potential new dangers.
- Standard protection: By default, Standard protection offers security from known dangers.
- No protection: GSB is turned off.
Enhanced protection mode
actively scans URLs, downloads, and browser activity to detect threats even before they are officially recognized.
When enabled, Enhanced Safe Browsing works by sending site URLs, small samples of page content to Google for real-time security checks.
Standard protection mode
By default, Google Chrome enables Standard Safe Browsing, which provides baseline protection against phishing, malware, and malicious extensions. Unlike Enhanced Safe Browsing, which actively scans all URLs in real-time, Standard Protection only reports suspicious sites and activities when a potential threat is detected.
2.3 How Standard Safe Browsing Works
When you visit a website, Chrome checks an obfuscated portion of the URL against Google’s Safe Browsing blacklist.
With standard protection, Chrome checks the sites that you go to, the extensions you have installed, and the files you attempt to download against Google's list of unsafe sites and downloads.
Each time you visit a website or attempt a download, Chrome first checks if the URL is on the list of safe sites stored on your device. If it's not, Chrome sends an obfuscated portion of the URL to Google. If Google confirms that the website or download is malicious, Chrome warns you that it may be dangerous with a red screen. In some cases, if the request to the privacy server fails or you're browsing in Incognito mode, the site gets checked against the list of unsafe sites stored on your device instead of the list stored with Google. In these cases, if there’s evidence of suspicious behavior, Chrome sends an obfuscated portion of the URL to Google.
In addition to the protections described above, Chrome will send a report to Google if it finds suspicious page behavior or suspicious actions. For example, when you enter a previously saved password on a new site, Chrome checks with Google to determine whether the page might be phishing. If it's determined that the site is phishing, Chrome asks you to check or change your password.
Sites are checked for phishing and social engineering terms. Chrome sends a small set of visual features to Google and compares the site to a list of dangerous sites to determine whether it's malicious. Some security features are disabled in Incognito to prevent revealing additional data to Google.
The fundamental workflow of the Google Safe Browsing crawler involves several key stages: discovering URLs, fetching the content associated with those URLs, and then meticulously analyzing this content for indicators of malicious activity. While the initial steps of discovering and fetching URLs are similar to standard web crawling processes, the Safe Browsing crawler incorporates additional, specialized analysis modules designed to identify security threats. This likely involves sophisticated parsing techniques and interpretation of web content to detect phishing attempts
The workflow of Google Safe Browsing Mechanism
In-depth
To truly understand how Google Safe Browsing (GSB) protects users — and how attackers can slip through the cracks — we need to dig deep into what happens on the client side (i.e., inside your browser). Most users don’t realize that Chrome is actively comparing visited URLs against a local copy of Google’s threat database in real time.
Here’s the workflow of Client-Side Detection:
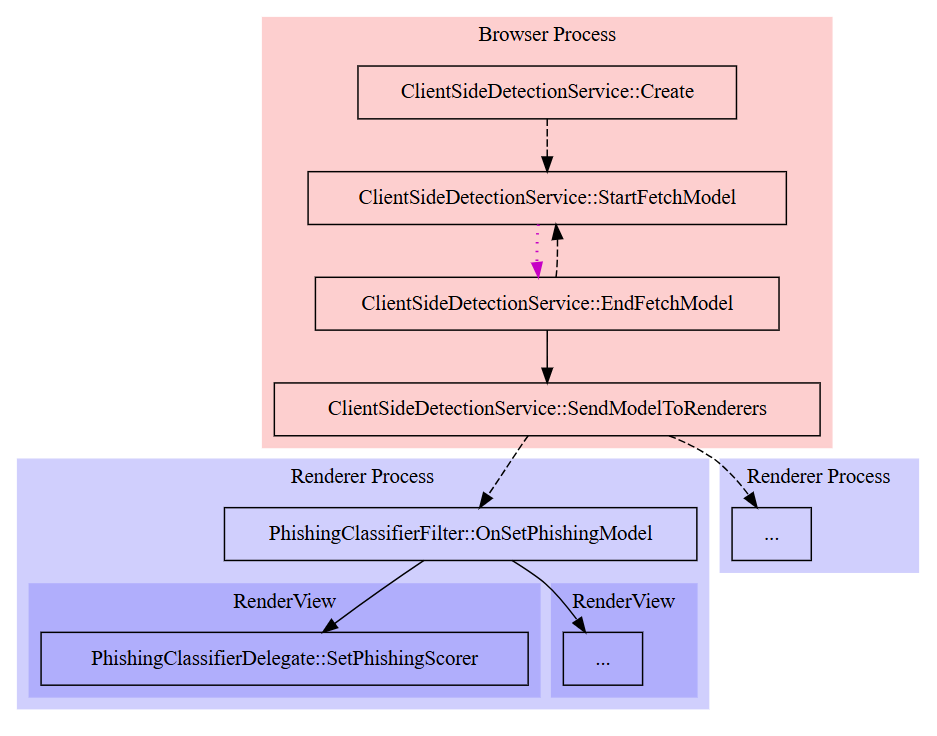
The images below show the flow when GSB requests for resource to detect a phishing attempt:
- Green Line → Safe pages are allowed instantly after a quick local check.
- Dashed Lines → Background (asynchronous) processes that check URLs further if needed.
- Dotted Magenta Lines → Requests to Google’s Safe Browsing server for full hash verification.
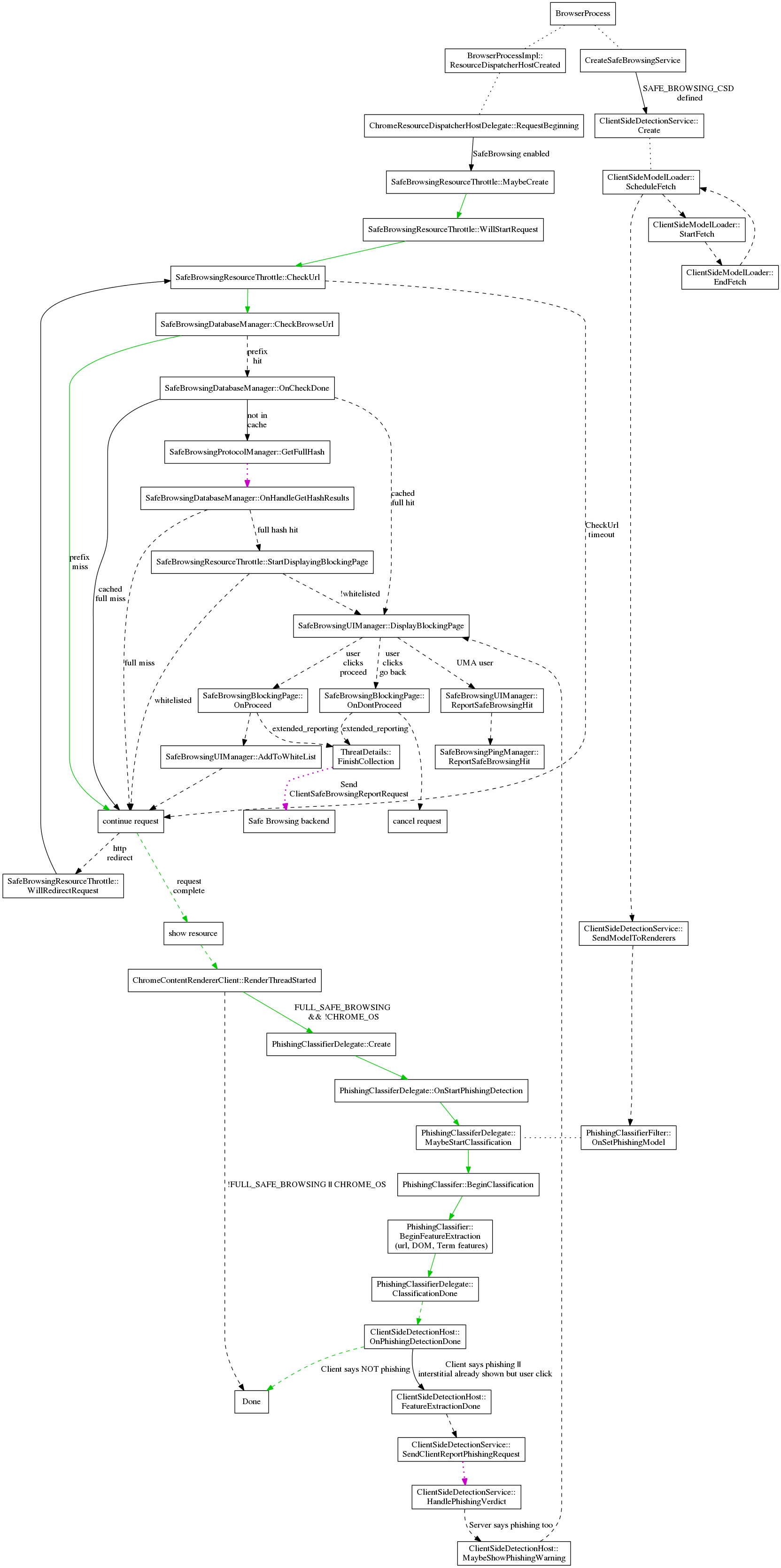
🔹 BrowserProcess & Initialization
BrowserProcess
This is the core of the Chrome browser process. Everything starts from here.
BrowserProcessImpl::ResourceDispatcherHostCreated
When the browser process starts, it creates a Resource Dispatcher Host, which is responsible for managing network resource loading (like HTTP requests).
🔹 Safe Browsing Integration in Request Lifecycle
ChromeResourceDispatcherHostDelegate::RequestBeginning
This gets triggered every time a new network request begins, like loading a new webpage or a resource.
At this point, if Safe Browsing is enabled, Chrome prepares to scan the request.
SafeBrowsingResourceThrottle::MaybeCreate
A "throttle" in this context is like a checkpoint that can delay or block a request. Here, Chrome decides whether to attach Safe Browsing logic to the request.
SafeBrowsingResourceThrottle::WillStartRequest
If it decides to go ahead, Safe Browsing is now officially monitoring the request. From this point, URLs can be checked against Google’s blacklists or models.
🔹 Safe Browsing Detection Service
CreateSafeBrowsingService
This step ensures that the entire Safe Browsing service is initialized. This includes checking malicious URLs, phishing detection, malware warnings, etc.
SAFE_BROWSING_CSD defined
This flag indicates that Client Side Detection (CSD) is enabled. This is important for phishing detection and behavioral analysis of websites locally on the user’s machine.
ClientSideDetectionService::Create
Creates the detection service that will do on-device evaluations of web pages for phishing or other malicious activity.
🔹 Loading the ML Model for Local Detection
ClientSideModelLoader::ScheduleFetch
Here, Chrome schedules a fetch of the machine learning model that will be used to evaluate websites client-side (offline/locally).
ClientSideModelLoader::StartFetch
Begins the actual download of the model from Google’s servers.
ClientSideModelLoader::EndFetch
Completes the fetch process. Once the model is ready, it can be used by the detection service for real-time analysis.
🔹How URLs Are Checked in Google Safe Browsing
SafeBrowsingResourceThrottle::CheckUrl
This method kicks off the actual security check on the requested URL. From here, the system begins scanning the URL against known malicious ones.
SafeBrowsingDatabaseManager::CheckBrowseUrl
This is where Chrome compares the URL’s hash prefix (first few bytes of the hash) against a locally stored list of dangerous URLs provided by Google.
- ✅ If there's no match (prefix miss): The URL is considered safe.
- ⚠️ If there’s a prefix hit (partial match): A deeper investigation is needed.
Learn more at:


SafeBrowsingDatabaseManager::OnCheckDone
If the prefix hit occurs, this step decides what to do next:
- If the full hash is already in the cache, it can proceed directly.
- Otherwise, it goes to the next step for full verification.
SafeBrowsingProtocolManager::GetFullHash
Now Chrome sends a request to Google’s servers to fetch the full hash of the suspicious URL to verify if it’s truly malicious.
This is privacy-preserving because:
- Chrome only sends hash prefixes, not full URLs.
- Responses are cached locally to avoid repeated server lookups.
SafeBrowsingDatabaseManager::OnHandleGetHashResults
This receives the full hash results from Google:
- ✅ If there's no full match, the URL is allowed.
- ❌ If there's a full hash match, it means the URL is confirmed dangerous, and it will trigger
SafeBrowsingUIManager::DisplayBlockingPage
Moreover, the Chrome browser includes a built-in phishing detection mechanism that analyzes the sum of all page pixels by color and compares it to the color palettes of sites the user has previously visited. You can learn more about how this works here:
https://blog.chromium.org/2021/07/m92-faster-and-more-effective-phishing-detection.html
In short, Google Safe Browsing uses a multi-layered detection strategy to flag phishing websites, combining both static and dynamic analysis. The three main techniques include:
✅ Page Content Analysis
GSB examines the structure and behavior of a webpage, looking at form fields, embedded scripts, login prompts, visual layout, and phishing-related keywords, to determine if the page mimics a legitimate service. This includes using machine learning models trained to detect deceptive behavior and UI elements.
✅ URL Reputation Matching
Every URL is hashed and checked against a massive database of known malicious or suspicious domains, maintained both locally on the client and centrally by Google. If a match is found — either directly or through a hash prefix — the page is blocked or escalated for deeper inspection.
✅ Visual Similarity Detection (Color Matching)
GSB can analyze color schemes to detect whether a phishing page visually impersonates a trusted website (e.g., Gmail, Facebook, or a banking portal). This method helps catch phishing sites that look legitimate at a glance, even if their domain doesn’t closely match the target brand.
Ref:
https://www.chromium.org/developers/design-documents/safebrowsing/

Google Safe Browsing Bypass...
Learn how real attackers bypass this mechanism
Google Safe Browsing is like a digital bouncer at the front door of the internet — scanning URLs, sniffing out suspicious content, and flashing red alerts when something feels off. But just like any bouncer, it’s not invincible.




