How to become a Pro Penetration Testing Intern

Introduction
In a world filled with cybersecurity threats, understanding and performing penetration testing (pentest) is not only a skill but also a crucial tool for protecting systems. Pentesting helps security experts discover vulnerabilities, assess risks, and suggest solutions before attackers can exploit them.
If you’re a beginner wanting to dive into the world of Ethical Hacking, this post is for you! We will build the first building blocks for your journey to becoming a true pentester – from foundational knowledge, essential tools, to an effective learning and practice roadmap.
Let’s start exploring the world of pentesting! 🚀
Challenges When Getting Started
When you first want to explore security or, specifically, pentesting, it can be a bit overwhelming because you're not sure where to start, or what skills you need to apply for pentesting positions or other entry-level security roles that involve assessment and testing.
Start
So, what foundational knowledge do we need to begin learning hacking?
Programming (~2 months)
This is a mandatory condition for you to go far in this field and in security in general.
To pentest something, you need to understand it deeply.
Essentially, you need to know how to create it, how user input data is processed by browsers and what phases it goes through.
I recommend starting with C programming to get a solid foundation in programming.
Once you’ve got the basics, focus on the main target. If you’re aiming for web application pentesting, you need to learn how to build web applications.
Learn how a web application is created:
- Front-End Programming: HTML, CSS, JS
- Back-End Programming: Node.js, PHP, Java, etc.
After understanding the basic flow of a web application, dive deeper into the practical implementation of code styles and structures, called Design Patterns. Some common patterns include:
- MVC: Model-View-Controller
- MVP: Model-View-Presenter
- Single-Page Application
Other terms include SSR (Server-Side Rendering) and CSR (Client-Side Rendering).
This gives you a comprehensive understanding of a web application’s flow.
Networking (~2 weeks)
In the early stages, you need basic knowledge of networking. There are two main concepts to understand:
- OSI Model: Understand how a packet is sent between devices.
- HTTP Protocol: Since you're focusing on web pentesting, understanding HTTP is crucial.
Key concepts include:
- HTTP request and response structure
- HTTP status codes
- HTTP headers
- HTTP/1 and HTTP/2
Operating Systems (~2 weeks)
Learning about Operating Systems (OS) is vital for entry-level pentesters because OS is the foundation of every computer system. I recommend practicing with the Bandit Overthewiew to get basic OS knowledge.
Bugs (~Unlimited)
After acquiring foundational knowledge of programming, networking, and operating systems, it’s time to learn about bugs—just like how a doctor needs to understand diseases, a pentester must understand bugs in computer security.
So, how to learn about bugs correctly?
The idea of “correctly” is subjective. Here, I’ll share how I learned about bugs, which I personally believe is “correct.”
Before learning specific bugs, you need to understand the root cause of most security vulnerabilities. That root cause is Untrusted Data – the birthplace of security flaws.
Most vulnerabilities arise when developers receive input from users and perform actions based on domain logic. But what happens if that input is not safe?
Untrusted Data refers to any input that a developer cannot guarantee is safe. From a programming perspective, data controlled by the developer is safe, but everything else is considered untrusted.
Once you understand this concept, you'll need resources with real-world vulnerabilities. I recommend three sources:
- PortSwigger: https://portswigger.net/web-security/all-topics
- TryHackMe: https://tryhackme.com/
- HackTheBox: https://www.hackthebox.com/
For every vulnerability, ask the following questions:
- What is the bug?
- How to detect it?
- How to test it?
- How to prevent it?
After understanding the basics of each vulnerability, continue reading case studies on platforms like HackerOne and Bugcrowd to gather ideas.
Now that you have foundational knowledge and real-life cases, the next step to truly understand vulnerabilities is Reproducing them.
Yes, we will recreate the vulnerabilities using case studies and ask why the application had that issue.
Some might ask, "How do I reproduce bugs?" Well, let me explain. 😅
To reproduce bugs and create a project that showcases your work on your CV:
- Build the base of your project and choose the type of application you're creating:
- You’ll need to learn Docker.
- Choose a back-end programming language.
- Decide on the type of application (e.g., blog, e-commerce site, or social network).
- For the front-end (FE), you can borrow templates to focus on server-side vulnerabilities (no need to build the front-end yourself).
- Recommended template sources: ThemeForest
- Choose a database.
- Build the base (entry point file, routing, DB connection).
- Init data (Create fixed data since you’ll be resetting your app often).
- Set up a page to control vulnerabilities.
Example:
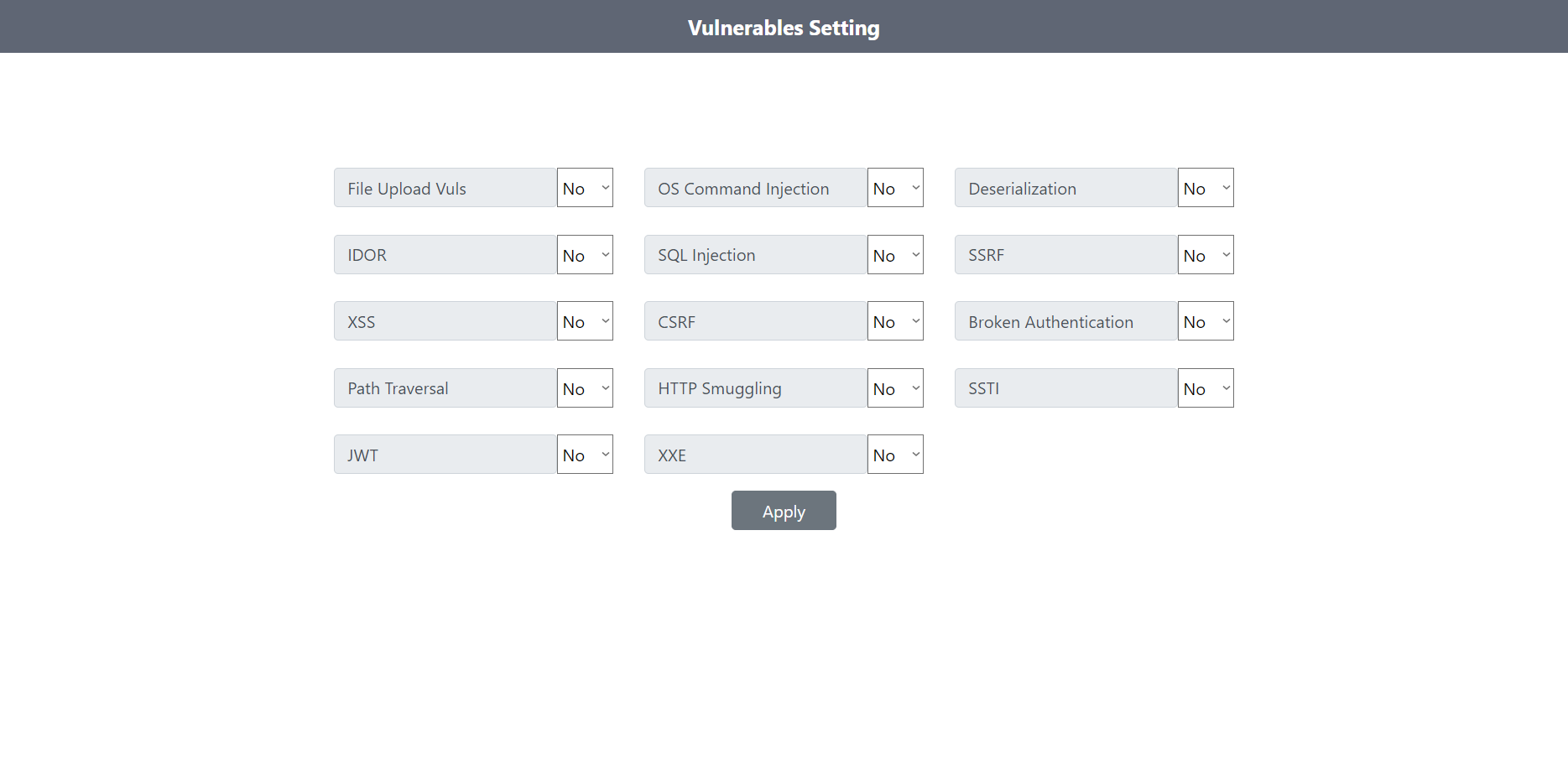
You'll have two modes:
- On: To reproduce the bug.
- Off: To prevent the bug.
- Write code and create scenarios that involve vulnerabilities.
After categorizing vulnerabilities, implement features in the app. For example, a login feature might be vulnerable to bypass authentication or SQL injection.
Once you’ve completed all the steps above, you can confidently apply for penetration testing internship positions at cybersecurity companies.
Conclusion
Becoming a pentester is not an easy journey, but with patience and continuous learning, you can prepare yourself well. A solid understanding of operating systems, networking, security, and pentesting tools will be the foundational steps for your growth in this field. Remember, there is no shortcut, but with passion and perseverance, opportunities will open up. Good luck on your journey to becoming a professional pentester!

