My first CVE story (CVE-2025-24372)

Introduction
Today is a special day for me, a CVE was released where I am the discoverer: CVE-2025-24372. I have my first CVE!
How to find
A while back, I discovered the XSS vulnerability of a website while doing the company's pentest project. Let’s call it redacted.com, and I saw this website was using ckan to manage data.
After being assigned the pentest project for the redacted.com website in the form of a black box, I just have URL of this website.
I performed dirsearch scan with my custom wordlist and found some interesting paths. One of which was /user/, after accessing this path, the website displayed the interface with the names of all the existing users in the website. As the photo below:
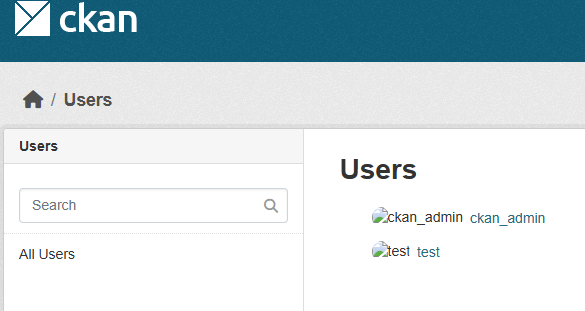
And from the usernames displayed I tried brute force with the commonly used wordlist password, after waiting for a while, as a result, I have found some accounts, I walked around and noticed that the accounts were all at minimum permissions and I found that all users could upload a profile picture for their account.
First, I tried uploading any jpg file, then tried to change the extension file to some malicious files, but the website does not allow uploading.
Then, after trying a few bypasses, I was able to upload any file by adding JPG file signatures to the top of the file content like this:
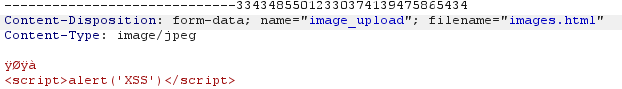
The website will allow upload, and this file will be saved at redacted.com/uploads/user/{file-name}.html
And when any user accesses that path, the script will be executed
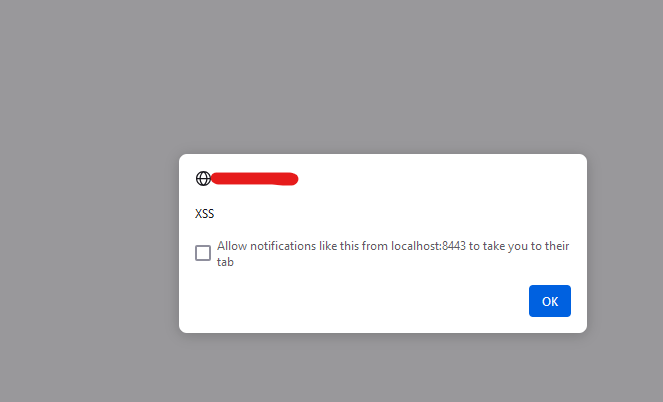
After submitting the report to my company, my leader said this is the CVE and
BOOM!
I had the first CVE that I didn't expect.
Reporting
After discovering that the XSS vulnerability I had just found was zero-day, I sought to enhance the impact of the vulnerability,
After a while, I was able to create a script that allows any user to become a sysadmin of the site with payload
ÿØÿà
<script>fetch("http://localhost:5000/ckan-admin").then(r=>r.text()).then(a=>fetch("http://localhost:5000/user/sysadmin", {method: "POST", headers: {'Content-Type': 'application/x-www-form-urlencoded'}, body: '_csrf_token=' + a.match(/name="_csrf_token" value=(.*)/)[1].slice(1,92) + '&username=testuser1&status=1'}).then(r=>r.text()));</script>After that, I wrote the report immediately and sent it to ckan through their email.
Timeline
23-12-2024: Report send.
16-01-2025: Accepted vuln
22-01-2025: Fixed
27-01-2025: CVE ID Received
05-02-2025: CVE published

