TeamTonTac SCC - Make your sysadmin life ...

Before getting into the blog, have you ever experienced the process of hardening a system? Or more specifically, hardening a newly built server to host an application? If so, this article is for you.

However, let me say first that we will not be discussing how to hardening here. We will discuss the issues that lie at the later stages of system hardening.

Oh come on, don't worry, I'll talk about the hardening process in the future ;)
So, what are the common post-hardening problems we encounter?
That's right! It's a matter of post-audit. Post-audit is the process of checking and reviewing the hardening that we have done. The goal of the post-audit is to evaluate the accuracy, compliance, efficiency and identify potential problems for future improvement. I know hardening a system has a lot of concerns. We are afraid of affecting the availability of the system, don't know where/when to start, what/how to do, blah blah blah so we often look for widely recognized standards, such as CIS Benchmark... Come on man, don't tell me you don't know what CIS Benchmark is 😔
CIS Benchmark is a set of security configuration guidelines developed by the Center for Internet Security (CIS). These guidelines are agreed upon by security experts worldwide, to help organizations, businesses, and individuals protect their systems, software, and networks from cybersecurity threats.
In short, CIS Benchmark will make your life more enjoyable. Trust me. All your headaches will be reduced (Not gone because there are many other problems)

Now, when it comes to using the guidelines that CIS provides us, it is entirely up to you to decide and implement it. This will have many issues related to large-scale deployment and centralized management (SCM). As I said before, I will mention these issues in the future.
Back to the main topic of this blog, which is related to the post-audit phase. The issue is compliance checking and optimization of the guidelines that CIS has guided us. I know it may seem redundant to double check that we've just hardened. But it's better than nothing, and it also helps provide evidence if your company is audited by a third party.
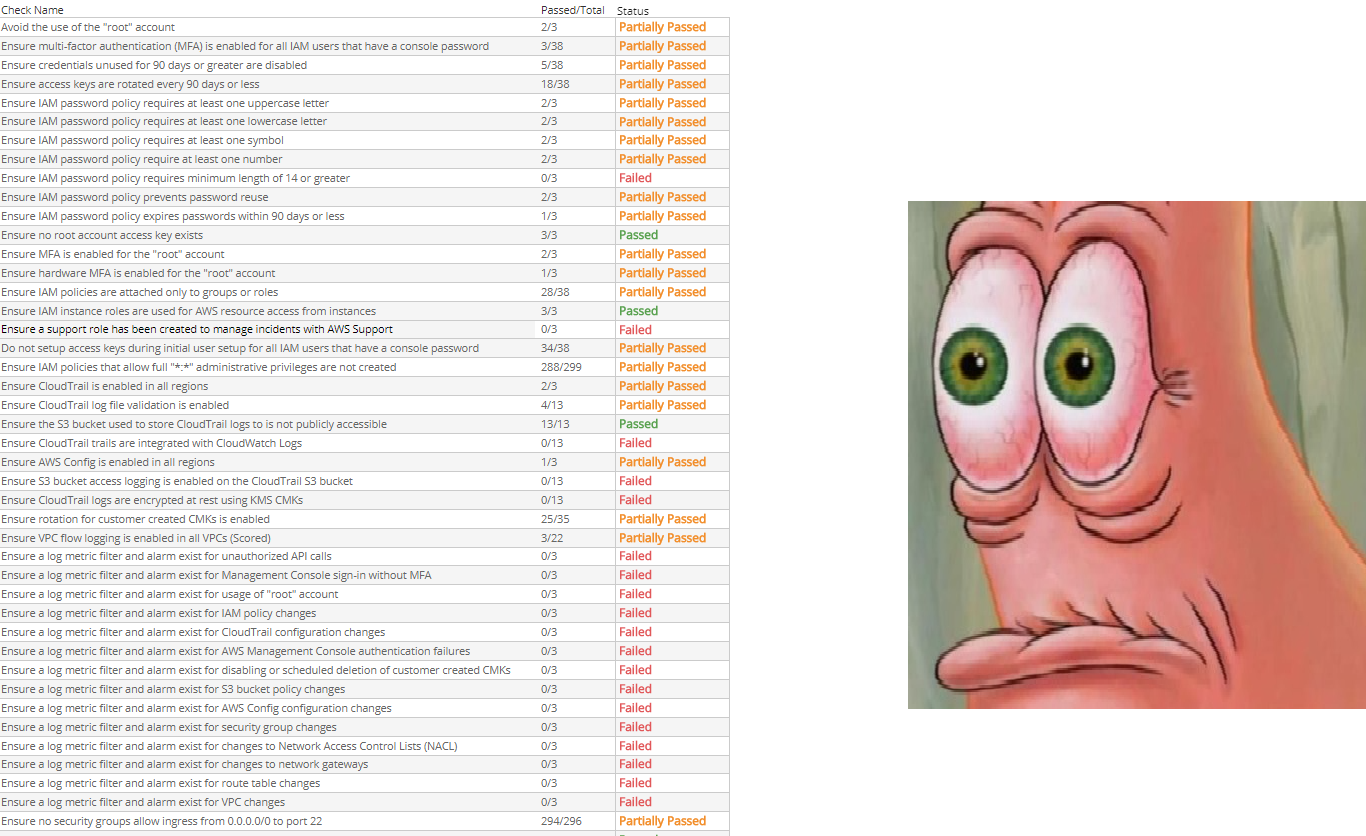
So, now we check it manually? Or what? Oh my friend, let me introduce you to TeamTonTac's new project. A SaaS that we call SCC. It was made to support you with compliance checks or security audits if you like.
Some of the features available:
- Interface for people who like minimalist style
- Supported objects: All versions of Windows and popular linux distros.
- Templates are CIS Benchmark profile level 1
- Show details of each item
- Support exporting formats: csv and pdf
- Supported languages: VI and EN
Your job is to execute the command that SCC provides, then return the data output. SCC will automatically analyze and give you the results in a flash.
If you tell me that I attached malicious code to the script that SCC created for you to execute then... you are an expert, you should analyze it yourself. Then you will realize that you wasted your time for nothing 🤣 Just try it. And I assure you I had no such intention.
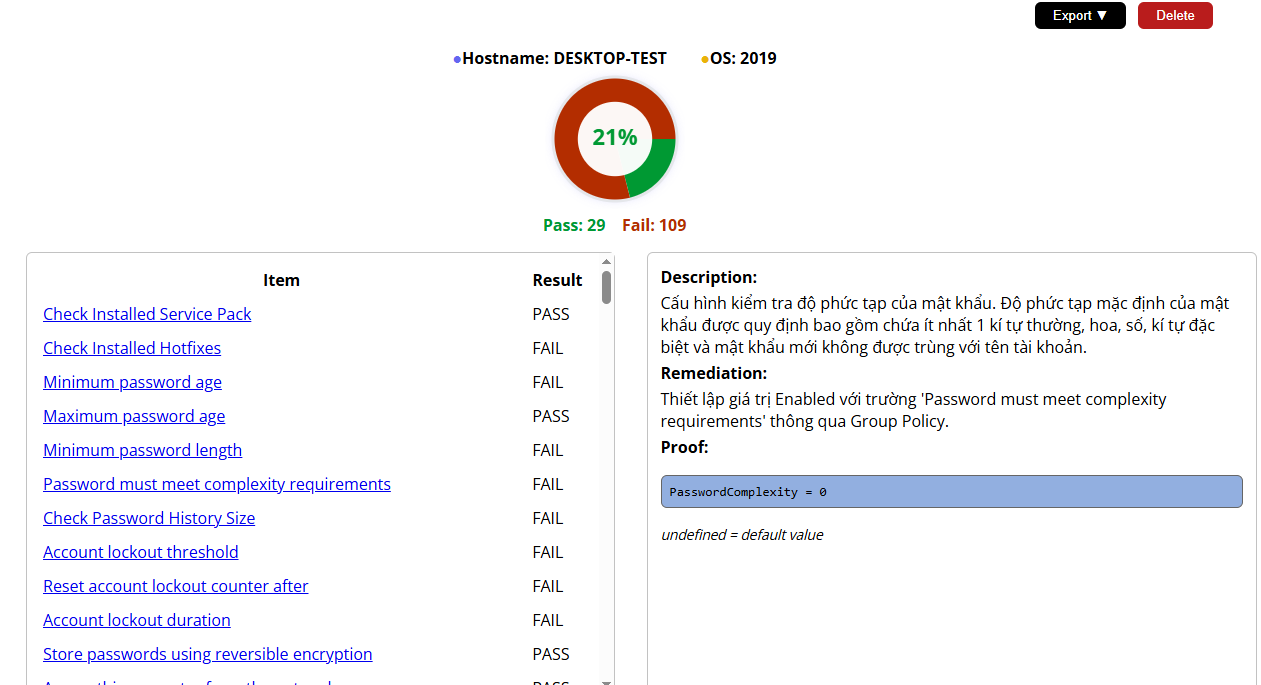
Below is the cover of a pdf file that SCC created, please take a look.

SCC is a new project so there are still many shortcomings and many unfinished features so I also need your feedback to improve it. In addition, I am also expanding SCC so that it can support more things such as other operating systems, databases, network devices, etc.
I am currently offering a free trial, if you are interested please contact me at contact@tontac.team
Thanks for reading this blog haha and see you later 🤪

